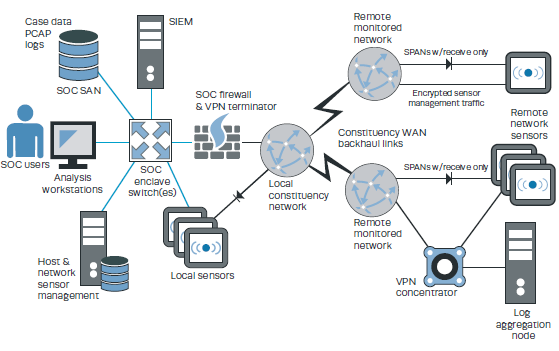
A SOC is able to execute its mission precisely because the adversary does not know where or how monitoring and response capabilities operate. SOC operators must assume that a compromise will happen at some point; therefore, it must operate in a non-trust environment while at the same time protecting critical information assets. The following figure from the Zimmerman manual (2014) shows the architecture of a protected SOC.
__________________________________
Reference:
Zimmerman, C. (2014). Ten Strategies of a World-Class Cybersecurity Operations Center. The Mitre Corporation.

 [pdf-embedder url=”http://c-market.us/site/wp-content/uploads/2017/06/Strategy-8.pdf” title=”Strategy 8″]
[pdf-embedder url=”http://c-market.us/site/wp-content/uploads/2017/06/Strategy-8.pdf” title=”Strategy 8″]