The drivers for cyber threat analysis and sharing analysis data are both regulatory and economic. The regulatory frameworks vary, based on jurisdiction. For example, in the U.S., data breach notification rules are typically set by state law. Network defenders performing incident response, cyber threat analysts characterizing threats, and malware analysts doing reverse engineering, all can share their analyses into their trust communities using the Threat Intelligence Platforms (TIPs).
There have been numerous studies in the past few years that survey or outline the emerging set of best practices for assessing cyber threats. Trade craft practices and common nomenclature have begun to emerge. This Toolkit resource points the reader to some of the most current recommendations in two separate and distinct areas:
- Cyber Threat Analysis
- Cyber Threat Intelligence Sharing
Colleges and universities all across the U.S. are developing programs to meet the growing need for a trained cadre of professionals that can bring knowledge and experience to these disciplines. The c-Watch program is aimed at accelerating the learning curve for analysts and threat hunters to begin to meet the critical shortfall in skilled workers.
Cyber Threat Analysis (CTA)
The threat landscape for people within public and private sector organizations has changed drastically over the past decade. Physical threats have diminished and cybersecurity threats have risen. At the same time the vulnerabilities of organizations have grown due to “bring-your-own-device” policies for cellular communications, distributed work forces, and the plethora of public cloud-based applications being used in the normal workflows of employees. Perimeter-based security from external threats is no longer sufficient to protect intellectual property assets, customer data, financial information or other key information resources. Cyber threats are even having broader geopolitical implications unimaginable only a decade ago. Cyber threat analysis (CTA) is an emerging skill set that takes advantage of certain best practices and tools to enhance the effectiveness of network defense.
The emergence of CTA as a separate discipline is a direct response to the growing threats that organizations face in the modern world. Certain models have arisen over the past decade that have shaped the narrative about what CTA is, how it contributes to intelligence as a separate field of study, and why it is so important when operating in the current socioeconomic and geopolitical context. These include, the Pyramid of Pain, the Hunting Maturity Model, the Intrusion Kill Chain and the Diamond Model, among others.
An ontology in common use among professionals in the field, also helps in understanding the complex interconnections between the adversary, his malicious infrastructure, victim targeting, and the extent of his capabilities. Categories of capabilities are typically broken into tools, techniques and procedures (TTPs), a useful framework for understanding the wide variety of methods used by threat actors in the cyber world.
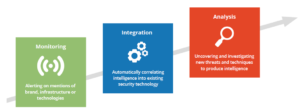
As far as tooling is concerned, the TIP is an aggregator of information and data for cyber threat analysis. But the real value-add of such a platform is its ability to ingest addition correlated information on indicators of compromise that a threat hunter is using to fingerprint the adversary and use it for data enrichment and analysis. The following diagram from a recent Recorded Future report on best practices shows how TIPs are now being used in both the Integration and Analysis stages.
Cyber Threat Intelligence Sharing (CTI Sharing)
A recent survey from the SANS institute provides a good summary of the key issues professionals face when seeking to share CTI.